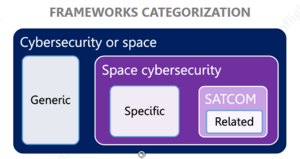
The Milestone 1 Meeting, held on October 15, 2025, marked a significant achievement for CyberInflight. With the completion of Task 1.2: Frameworks Identification, we successfully reached a key point in our journey. It was a moment of great accomplishment, as we presented our findings and outlined the next steps in the project. We refer to “framework” as a text covering a specific topic or domain. The approach and structure of the document are centered around requirements or best practices. A framework can come as a regulation, an act, a directive, a law, a standard, or a guide.
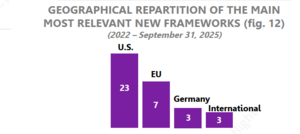
During this milestone, we proudly shared the results of our comprehensive identification process, which encompassed more than 170 cybersecurity frameworks sourced from over 60 entities. Out of those frameworks, around 50% are generic, around 40% are dedicated to space cybersecurity, and around 10% are directly related to SATCOM. The diversity of these frameworks highlights the broad spectrum of resources available to ensure the SATCOM ecosystem remains resilient in the face of emerging threats. We then narrowed down the list to around 80 frameworks with Priority Order 1 or 2, provided by more than 25 different entities. These priority frameworks are organized by common types of activities, including Security Operations, Governance & Maturity, and Security & Risk Assessment. In some cases, frameworks can focus on several types of activities. In that case, the framework is referenced in the most relevant type of activity. Of these Priority 1 and 2 frameworks, around 50% of the frameworks focus specifically on space cybersecurity, around 35% are generic, and around 15% are directly related to SATCOM. With Task 1.2 now completed, we have a solid foundation to move forward in the next phase of the project. Our framework identification and categorization have set the stage for a deeper dive into the most relevant frameworks, ensuring that no stone is left unturned. To make sure we reach a comprehensive database gathering cybersecurity frameworks, we make sure the database if not fixed and it can evolve if new cybersecurity frameworks are identified throughout the mission.